Artigo arquivado! É somente leitura
Testing Intermediary Concealment: Essential Strategies and Instruments
6 de Abril de 2025, 13:18 - sem comentários ainda | Ninguém está seguindo este artigo ainda.In the digital age, maintaining anonymity on the internet has become essential for both individuals and businesses. Regardless of whether you are scraping data, conducting market research, or merely seeking to enhance your privacy, comprehending how to efficiently use proxies is crucial. Proxies serve as middlemen between your device and the internet, allowing you to browse while hiding your actual IP address. However, not all proxies are designed the same. It's vital to evaluate proxy anonymity and determine their effectiveness in to maintain a secure online presence.
This article will examine key methods and tools for evaluating proxy anonymity. We will delve into various types of proxy harvesters and checkers, how to create quality proxy lists, and the differences between various protocols such as HTTP, SOCKS4, and SOCKS5. Whether you are looking for a fast proxy scraper for web scraping or in search of the top free proxy checker for 2025, we will offer you with the knowledge needed to enhance your online activities. Come along as we explore through the top practices for finding and verifying high-quality proxies suited for your requirements.
Grasping Proxy Types
Proxy servers act as intermediaries between clients and the internet, enabling for various kinds of inquiries and responses. The typical types of proxy servers are HTTP, Hypertext Transfer Protocol Secure, SOCKS4, and SOCKS version 5. HTTP proxy servers are crafted particularly for web traffic, handling inquiries made through browsers. HTTPS proxy servers provide an additional layer of protection by encrypting the data transferred, rendering them a popular option for ensuring privacy while browsing.
On the other hand, SOCKS proxies, which exist in versions 4 and 5, are more flexible. SOCKS4 supports TCP connections and is suitable for simple functions, while SOCKS5 enhances capabilities by allowing both TCP and UDP protocols. This feature renders SOCKS version 5 proxies perfect for activities that require a wider variety of uses, such as streaming and file transfers. Understanding these differences is vital for selecting the right proxy server for particular requirements.
In considering proxies for tasks like web scraping or automation, distinguishing between private and shared proxies is important. Private proxies offer exclusive access to a single user, offering better speed, security, and reliability. Shared proxies, while often free and readily accessible, can be slower and less secure due to many clients sharing the same IP location. Understanding the types of proxies and their characteristics helps users choose the best option for their tasks.
Key Techniques for Proxy Scraping
Regarding proxy scraping, a highly effective method is using specialized proxy scrapers that are to collect proxies from multiple sources on the internet. Such tools can be configured to target specific websites known for free proxy lists, and they can streamline the collection process to save time and effort. A good proxy scraper should support both HTTP and SOCKS proxies, providing a wide range of options for users based on individual needs.
Another important technique is to validate and check the proxies that have been scraped. This involves using a reliable proxy checker or verification tool which tests each proxy for privacy, speed, and the capability to handle requests successfully. The best proxy checkers can provide real-time results and classify the proxies as public, private, or anonymous, which is crucial for optimizing the performance of web scraping tasks and avoiding blocks.
Moreover, it's crucial to stay informed on the quality and sources of proxies. Utilizing online tools and forums focused on sharing proxy lists can help find high-quality proxies. Regularly checking the status of known proxy lists and employing a mix of free and paid options will improve the overall effectiveness of proxy scraping. By integrating these techniques, users can create a robust strategy for collecting and utilizing proxies for various applications such as web scraping and automation.
Analyzing Proxy Privacy
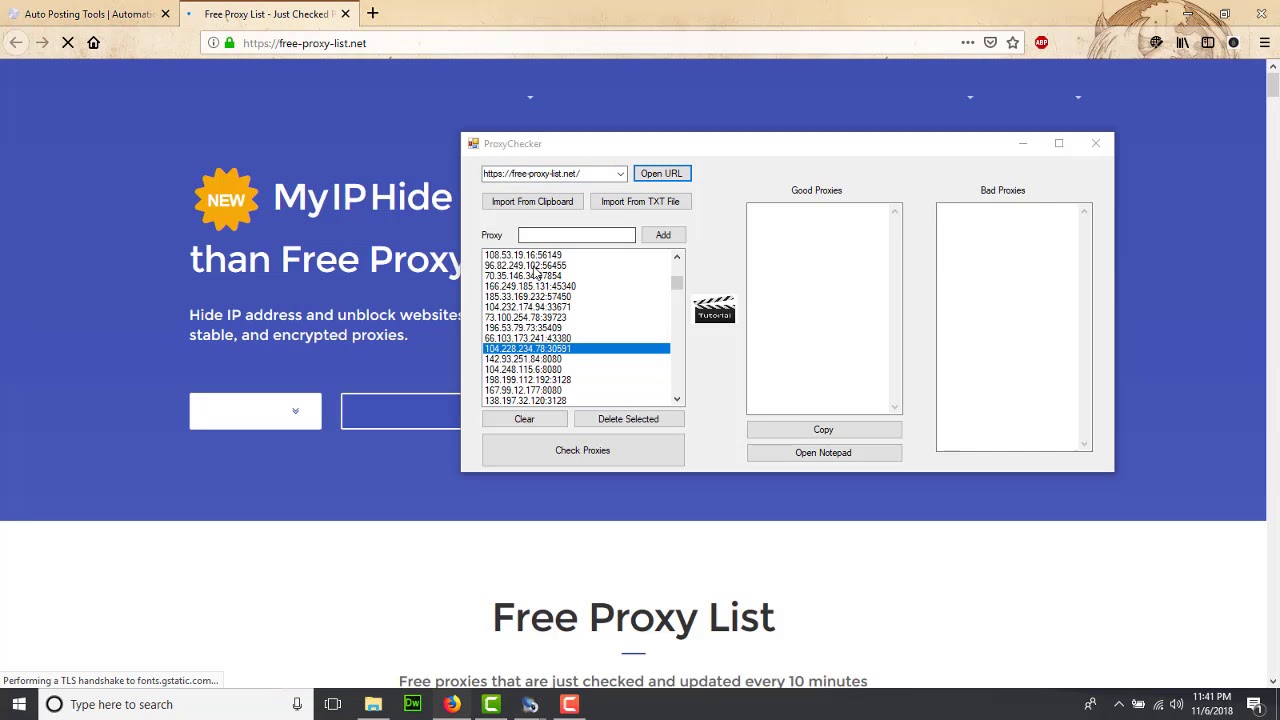
As utilizing proxies in web surfing or web scraping, grasping proxy anonymity is critical. Proxies fulfill various purposes, such as hiding your original IP address and overcoming geographic limitations. Yet, not all proxies deliver the same level of anonymity. The three types of proxies are clear, hidden, and elite proxies, each providing varied levels of protection. Transparent proxy servers expose your IP address to the target website, whereas anonymous proxies conceal it but may be identified. High-level proxies deliver the highest level of privacy, making it almost difficult for websites to detect the user.
To determine the level of obscurity a proxy server delivers, users can employ various techniques. One frequently used method is to examine the proxy server's behavior through multiple privacy tests available online. These tests analyze the header responses returned by the proxy. Utilities that carry out a detailed examination can indicate whether the proxy server is clear or hidden based on the information it sends. Furthermore, conducting performance tests together with these assessments can help determine whether the proxy server's speed meets the needs of the intended task.
As selecting proxy servers, it is essential to take into account their origin and reputation. Many open proxies may claim to be hidden but can be compromised or insecure. Premium proxies, typically available for a cost, generally provide superior safety and stability. Individuals should use trustworthy proxy checkers that can confirm both the privacy and performance of the proxies. This meticulous evaluation ensures that you preserve anonymity while efficiently using proxies for data extraction, SEO tasks, or automation processes.
Top Proxy Solutions and Assets
As diving into the realm of proxies, having the right tools and resources is vital for effective web scraping and anonymity testing. Proxy scrapers are at the cutting edge, allowing users to gather collections of proxy servers quickly. Some notable options consist of complimentary proxy scrapers that provide entry to proxies without associated cost, while fast proxy scrapers enable individuals to acquire quick proxies efficiently. Software such as ProxyStorm.com also deliver extensive solutions for scraping proxies tailored to user needs, making it more convenient to maintain an updated and dependable proxy list.
Validation and verification of proxies are similarly important, which is where proxy verification tools come in. The top proxy checkers can help validate whether proxies are operational, checking their performance and privacy levels. Whether individuals require an HTTP proxy checker or a SOCKS proxy checker, there are tools designed specifically to provide reliable information about the proxies in use. For those keen in performance, the top free proxy checkers for 2025 are surfacing as strong tools to ensure proxies meet performance standards prior to use.
Finally, finding top-notch proxies is essential for optimizing web scraping performance. To assist this, online proxy list generators can aid individuals generate custom lists tailored to particular requirements. Additionally, a range of SEO tools with proxy support can help in automating tasks while using both private and shared proxies. Grasping the distinctions between HTTP, Socket Secure 4, and SOCKS5 proxies can also direct users in selecting the best options for their specific applications, ensuring they gather data efficiently while preserving anonymity online.
Top Practices for Website Data Extraction with Proxy Servers
As involving in web scraping, it is crucial to choose the right proxy servers to ensure both efficiency and safety. Utilizing a mix of private and open proxies can help harmonize the demand for concealment and speed. Dedicated proxies generally offer superior performance and stability, while shared proxies can be employed for non-critical tasks. It’s advisable to regularly switch proxies to diminish the risk of IP bans and keep a consistent scraping rate. Tools like proxy collecting tools and lists of proxies can streamline the operation of sourcing and managing proxies for your projects.
Another important aspect is to track the effectiveness of your proxy servers. Using a reliable proxy validator or proxy verification tool helps validate speed and privacy levels. Regularly evaluating proxies allows you to spot lagging or non-functional IPs before they hinder your scraping efforts. Additionally, comprehending the variations between types of proxies, such as HTTP, SOCKS4, and Socket Secure 5, can optimize your scraping strategy, enabling you to pick the ideal choice for your individual needs.
Finally, honoring the target site's policies is essential. Always implement polite scraping practices, such as establishing appropriate request intervals and being mindful of the data extraction limits. This not only helps avoid IP bans but also ensures a responsible approach to data extraction. By complying with these effective practices, you can achieve successful web scraping while minimizing interference to the target site's operations.
Free vs Free Proxy Services
When considering proxies for web scraping or online privacy, one key factor is whether to use free or premium proxy solutions. Free proxies often lure users with the offer of no cost, making them an appealing option for individuals or limited projects with tight budgets. However, these no-cost services usually come with significant drawbacks, such as slower speeds, lower reliability, and a increased risk of being blacklisted. Additionally, no-cost proxies may lack robust security features, putting users to potential information breaches or malicious activities.
On the flip side, premium proxy services offer numerous advantages that can greatly improve user satisfaction and outcomes. best proxy tools for data extraction provide faster connection speeds, more consistent uptime, and a bigger pool of IP addresses to choose from. Paid proxies can also offer better anonymity and privacy safeguards, reducing the chances of getting detected and blocked by sites. Many premium services include additional features like sophisticated geo-targeting, dedicated IP addresses, and customer assistance, making them a more suitable choice for dedicated web scraping and robotics tasks.
Ultimately, the choice between free and paid proxy solutions depends on your specific needs and circumstances. If your project requires high availability, safety, and efficiency, investing in a trusted paid proxy service may be the best choice. However, for casual individuals or those just experimenting with proxies, starting with no-cost options can provide a fundamental understanding of how proxies function, with the possibility to transition to premium services as requirements evolve.
Future Innovations in Proxy Solutions
The landscape of proxy technology is continually evolving, with improvements aimed at enhancing safety and privacy. One key development is the move towards definitely sophisticated encoding protocols, which seek to secure user information while employing proxy services. As security worries rise, both users and businesses will progressively demand proxy solutions that provide robust protection measures, making it crucial for proxy service providers to remain competitive by implementing advanced encryption methods.
Another emerging trend is the inclusion of artificial intelligence and automated learning in scraping proxies and validation tools. AI algorithms can enhance the effectiveness of proxy scrapers by streamlining the recognition of top-tier proxy solutions and eliminating poor ones. This technology also allows improved assessment of proxy performance, allowing individuals to rapidly determine the ideal proxies for their needs. As a result, we can expect seeing more advanced proxy verification tools that leverage AI for faster and better results.
Finally, the shift towards distributed proxies is increasing, driven by the requirement for increased openness and authority in internet usage. Distributed networks allow users to contribute their excess internet bandwidth, creating a more resilient and spread out network of proxies. This not only enhances secrecy but also tackles problems related to monopoly and accessibility of proxy solutions. As this trend continues, clients will have expanded alternatives for accessing premium, private proxies without only depending on standard companies.
0sem comentários ainda