¡Artículo archivado! Es de solo lectura
The Prospects of Proxies: Trends and Forecasts for the Year 2025
abril 6, 2025 12:35 - no comments yet | No one following this article yet.Within the quickly changing environment of the web, proxies have turned into essential resources for a range of uses, from improving internet privacy to facilitating effective web scraping. As to 2025, understanding the future of proxies and the trends shaping their utilization is crucial for people and companies alike. The need for proxy scrapers and checkers is predicted to increase as an increasing number of users look for efficient solutions for navigating the challenges of data extraction and online anonymity.
With advancements in technology, the resources available for managing proxies—such as complimentary and quick proxy scrapers, proxy validating tools, and trustworthy proxy list generators—are becoming more advanced. There is a rising need to differentiate between HTTP, SOCKS4, and SOCKS5 proxies, as they each offer distinct capabilities tailored to different tasks. While we investigate the best practices and resources for scraping and verifying proxies, we will also emphasize the significance of understanding the distinctions between private and public proxies, as well as the ongoing debate between no-cost versus premium options for web scraping.
Summary of Proxy Solutions
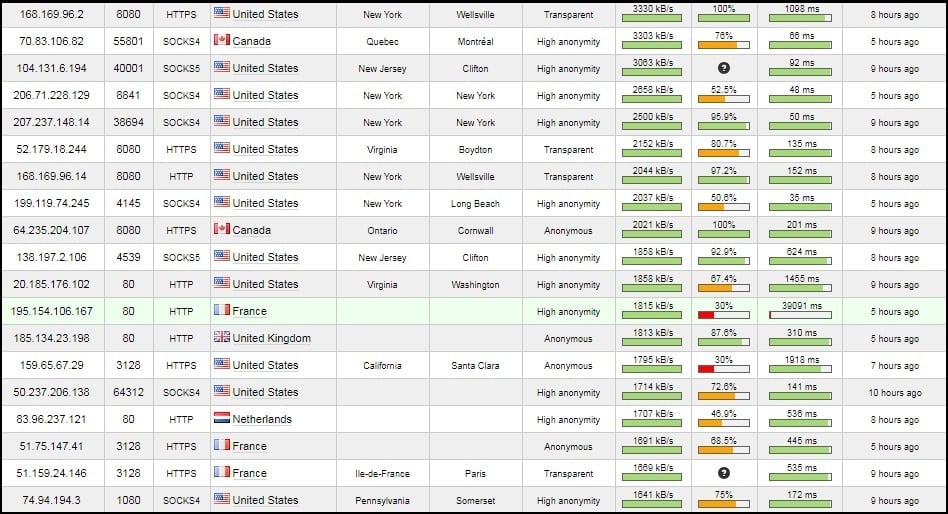
Proxy solutions play a vital role in the effectiveness and performance of data scraping and data extraction tasks. A range of tools, including proxy harvesting tools and proxy validation tools, are designed to help users gather, verify, and organize proxy lists efficiently. With the growing need for data scraping, the use of proxies has become crucial in circumventing restrictions, ensuring privacy, and improving speed during information gathering processes.
One key aspect of proxy tools is their capability to provide lists of free or premium proxy servers. Complimentary proxy scrapers can be effective resources for acquiring functional proxies, although they frequently come with limitations in terms of quality and reliability. Rapid proxy tools, on the other hand, focus on efficiency and efficiency, facilitating quick collection of proxy information that can be immediately utilized for data extraction purposes. Additionally, validation services are critical in assessing the effectiveness and anonymity of proxies, ensuring that users can choose the most suitable options for their specific needs.
As the environment of data extraction evolves, so too do the proxy solutions available in the industry. New advancements in tech are resulting in the development of more advanced tools, such as HTTP proxy scrapers and SOCKS proxy checkers, which address varied consumer needs. The importance of choosing top-notch proxies for SEO tools and automation tasks cannot be emphasized enough, as this can greatly impact the success of information gathering efforts. With ongoing developments towards better performance and usability, the outlook of proxy tools looks promising.
Developments in Proxy Server Utilization
The rising demand for data privacy and protection is prompting a increase in proxy usage across various industries. As a growing number of individuals and businesses acknowledge the importance of safeguarding their digital activities, proxies have become essential tools for preserving anonymity. This movement is particularly clear in fields that require data scraping, where employing proxy systems ensures that data extraction stays undetected and in line with site policies.
Another significant movement is the increasing reliance on automated for web scraping. Organizations are looking for faster ways to gather data, leading to the development of cutting-edge proxy system scrapers and checkers. Rapid proxy server scrapers are becoming essential for real-time data gathering, permitting businesses to keep their information current without the threat of IP bans. Furthermore, the emergence of cloud-based solutions allows seamless integration of proxy tools with existing processes, making it more convenient for users to access and manage their proxy lists.
Furthermore, the difference between free and dedicated proxy systems continues to be crucial for users seeking for reliable connections. Numerous are opting for private proxy systems for their enhanced speed and anonymity, while public proxy systems are being utilized for less sensitive tasks. The development of search optimization tools with proxy support also demonstrates this movement, as marketers use proxy servers for automated in online marketing, examining competitors, and carrying out market research without disclosing their true identity.
Top Practices for Proxy Scraping
While engaging in web scraping with proxies, it can be essential to emphasize the standard of the proxy servers you choose. Using reliable providers is essential, as this ensures better functionality and minimizes the likelihood of coming across non-functional or underperforming proxies. Conduct thorough research to identify the most effective proxy sources for web scraping. Evaluate the options of public and private proxies, as each has its advantages and drawbacks. Paid proxies usually provide a consistent and speedier operation, while public proxies can be available without charge but may have potential drawbacks.
A further important factor is the consistency of checking proxies before use. Using a strong proxy validator can maximize productivity and enhance the overall efficiency of your scraping tasks. Consistently verify the quickness and anonymity of the proxies you have acquired—this will help ensure that they meet your specific needs. Utilities like the best no-cost proxy checker for 2025 can help in assessing the performance and dependability of proxies.
Additionally, employing automated processes using proxy scraping tools can considerably enhance your process. Using difference between HTTP SOCKS4 and SOCKS5 proxies in languages like Ruby for scraping tasks can simplify the workflow of gathering and testing proxies. Formulate a plan for how to harvest proxies for no cost while maintaining best practices. This helps in locating top-notch proxies without jeopardizing your current assets, promoting effective web scraping and information retrieval.
Proxy Verification Methods
Verifying proxy addresses is important for guaranteeing that they function reliably and satisfy the specific demands of users. One effective strategy is to use proxy checkers that evaluate different factors such as data transfer speed, anonymity level, and connectivity. These applications help in identifying whether a proxy server is operating correctly and can offer the necessary performance measures. Rapid scraping tools often come with internal authentication tools to streamline this procedure, enabling users to eliminate slow or slow proxies before utilizing them for data extraction or other activities.
Another significant approach for verifying proxies is evaluating the anonymity of proxy servers. This can be achieved through specialized tools designed to test whether a proxy exposes the user's original Internet Protocol address or if it operates as a high-anonymity service. Understanding the difference between Hypertext Transfer Protocol, SOCKS version 4, and SOCKS5 proxy servers is essential in this context, as each category can provide diverse degrees of privacy and protection. Individuals should choose a proxy server based on their privacy requirements, especially when participating in automation or data extraction tasks.
In conclusion, assessing the performance of proxy servers is crucial for applications that demand fast link speeds, such as scraping large volumes of data in instantaneously. Clients can use speed testing tools specifically designed for checking the performance of proxies. By tracking delays and download speeds, users can figure out which proxies are best suited for their requirements. Furthermore, utilizing a proxy list tool can help users curate and regularly maintain a list of high-quality proxies, guaranteeing best performance for their particular needs.
Anonymity and Types of Proxies
Identity protection is a vital aspect when using proxies, as it helps safeguard user identity and data from prying eyes. Proxies can be classified primarily into three types: transparent, anonymous, and elite proxy servers. Clear proxies do not hide the user's internet protocol address and can be easily detected, making them inappropriate for tasks requiring anonymity. On the other hand, anonymous proxies enable users to surf the web without revealing their actual internet protocol address while still identifying themselves as proxy users. High-anonymity or elite proxies provide the utmost degree of privacy, masking the user's identity completely, making it incredibly difficult to determine whether a proxy is being used.
One frequent point of misunderstanding is the distinction between HTTP, SOCKS4, and SOCKS version 5 proxies. HyperText Transfer Protocol proxies are designed specifically for internet traffic and effectively handle web requests. SOCKS4 and SOCKS5 proxies, however, are more flexible, as they can forward any traffic type, not just web traffic. SOCKS version 5 supports extra functionalities such as user verification, which enhances anonymity and safety. While both SOCKS4 and SOCKS version 5 proxies provide solid identity protection, SOCKS version 5 is generally favored for tasks demanding a greater degree of security and confidentiality.
When selecting proxies for web scraping or automated tasks, understanding the level of anonymity provided by different types can significantly impact success. For tasks that require quickness and dependability, such as web scraping, using high-anonymity proxies is recommended. Additionally, finding top-notch proxies from trustworthy providers, whether no-cost or premium, plays a crucial part in achieving optimal anonymity. As businesses and individuals increasingly depend on proxies for data collection and privacy, the choice of type of proxy and the understanding of their capabilities will continue to be crucial in navigating the digital landscape effectively.
Price Comparison: Free vs Premium Proxies
Regarding proxies, the initial considerations for users is whether to select complimentary or paid choices. Complimentary proxies are attractive due to their zero upfront cost, making them an attractive choice for individuals and small businesses with tight budgets. However, complimentary proxies often have several downsides, including slower speeds, unreliable connections, and potential security risks. Users may find that these proxies are clogged with traffic, resulting in poor performance and frequent disconnections.
On the other hand, premium proxies usually provide a greater stable and secure experience. Suppliers of paid proxies often invest in better infrastructure, allowing for enhanced speeds and more reliable connections. Additionally, the majority of paid services include customer support, which can be essential for troubleshooting issues. With superior quality and dedicated servers, users can expect better anonymity and better overall performance, especially for tasks such as web scraping or data extraction.
Ultimately, the determination between complimentary and premium proxies should be based on unique needs. For occasional users or those engaged in low-stakes browsing, complimentary proxies may suffice. However, for businesses relying on consistent proxy performance for SEO tools, automation, or extensive web scraping projects, investing in paid proxies is generally the wiser choice. The long-term benefits of reliability and speed can outweigh the initial cost, leading to more effective and efficient outcomes.
Projected Predictions for Proxy Technologies
As we advance towards 2025, the landscape of proxy technologies is expected to evolve notably. Improvements in scraping proxies will probably enhance their features, enabling users to gather proxies more effectively and consistently. With the demand for rapid connections rising, the development of quick scraping tools that can process high amounts of calls will become vital, particularly for scraping the web and data gathering tasks. This demand will propel advancements in software tools that identify and harvest proxy servers from various sources, making sure that users can obtain current and operational proxy lists.
The increase of automated technologies in different industries will shape the way proxies are utilized. More search engine optimization tools and software will integrate support for proxies, enabling businesses to streamline different tasks such as gathering information and market analysis. As businesses seek to keep their superiority, the focus will transition to proxies that are private that provide enhanced protection and privacy, differentiating them from proxies that are public. This pattern will call for the development of sophisticated tools for verification that ensure the proxies are not only quick but also maintain user anonymity during use.
Lastly, as the significance of data privacy and security continues to increase, we can foresee tighter regulations controlling the use of proxies. Users will increasingly need robust instruments, such as checkers for proxies and verification systems, to determine both velocity and privacy. The disparity between HTTP, SOCKS version 4, and SOCKS5 proxy servers will grow more obvious, with users looking for specific capabilities based on their needs. As a result, a wider array of sources of proxies will surface, contesting to provide reliable and reliable proxies tailored to the varied requirements of companies and personal clients alike.
0no comments yet